Cloud-native Endpoint Security That Adapts To Your Need
The majority of today’s cyberattacks now encompass tactics such as lateral movement, island hopping and destructive attacks. Advanced hacking capabilities and services for sale on the dark web compound the issue. These realities pose a tremendous risk to targets with decentralized systems protecting high-value assets, including money, intellectual property and state secrets.
While other endpoint security products only collect a dataset related to what is known bad, our solution continuously collect endpoint activity data because attackers intentionally try to look normal to hide their attacks. Analyze attackers’ behaviour patterns to detect and stop never-seen-before attacks.
You need an endpoint security platform that helps you spot the minor fluctuations that hide malicious attacks and adapt prevention in response.
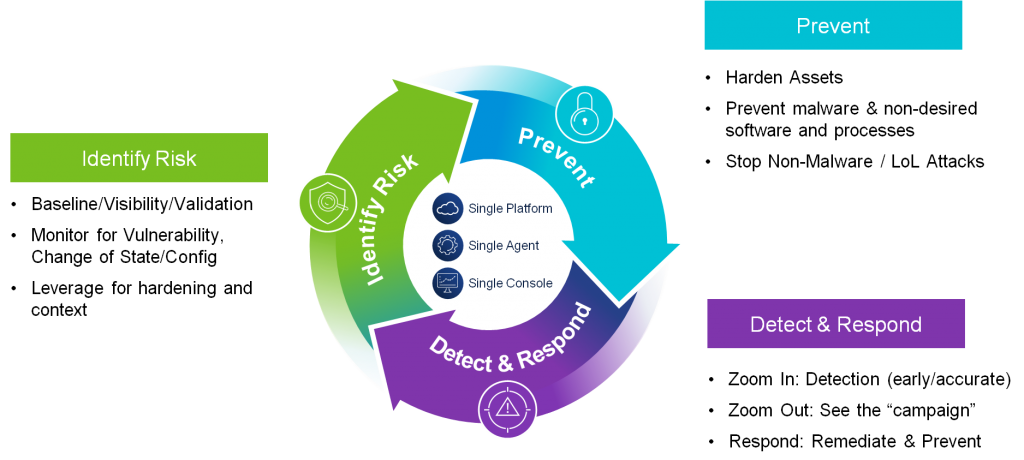
Next-Generation Endpoint Security and Behavioral EDR
Protect your organization and customer data with an easy-to-manage, cloud-native endpoint security platform that combines prevention and automated detection to defend your organization from today’s advanced cyber attacks.
Application Control and Critical Infrastructure Protection
Lock down servers and critical systems, prevent unwanted changes and ensure continuous compliance with regulatory mandates. Leveraging cloud reputation services, IT-based trust policies and multiple sources of threat to ensure that only trusted and approved software is allowed to execute on an organization’s critical systems and endpoints.
Threat Hunting & Incident Response for Hybrid Deployments
An incident response and threat hunting solution designed for security operations centre (SOC) teams with offline environments or on-premises requirements. The solution continuously records and stores comprehensive endpoint activity data, so that security professionals can hunt threats in real time and visualize the complete attack kill chain. It leverages on threat intelligence, which is applied to the endpoint activity system of record for evidence and detection of these identified threats and patterns of behaviour.
Real-Time Device Assessment & Remediation
By providing administrators with real-time query capabilities from a cloud-native endpoint security platform, the solution enables teams to make quick, confident decisions to harden systems and improve security posture. The solution closes the gap between security and operations, allowing administrators to perform full investigations and take action to remotely remediate endpoints all from a single solution.
Read More: Application Control and Critical Infrastructure Protection





