Centralized, Simplified and Versatile Key Management
The hardest part of implementing strong encryption is securely and effectively managing keys and certificates. Hackers don’t break encryption, they steal keys. Without strong and flexible systems in place to do that, the best encryption standards are useless.
Managing cryptographic keys, certificates and the policies that govern them is a continual challenge — and gets even more complex when the cloud is added to the equation. The key management solution offers 5 essential elements of an effective key lifecycle management that will alleviate many of the problems, both now and in the future:
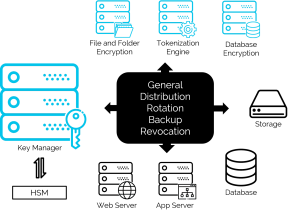
Fig. Flexible key management – on premise or in the cloud
Separation of Duties
Ensures that different people control different procedures so that no one person has full control over the platform. Dual control requires that at least two people control a single process.
Centralized Control
A centralized solution to implement consistent policies across all encrypting systems, while assigning and managing attributes on keys and certificates that are specific to the end-user device or application
Comprehensive Logging
Keeping comprehensive event logs and ALL audit trails is another core component of key management where reports for audit and policy operations can be scheduled and produced.
Integrate & Unify
A single platform that offers flexible integrations to applications using Key Management Interoperability Protocol (KMIP), APIs, ready connectors to databases and Windows/Linux servers with multi-vendor HSM support.
Read More: Key Management FAQ





